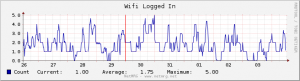
The good news is this – we’re now up to 30 subscribers on the neighborhood wifi.
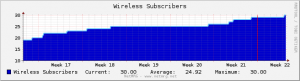
With an average of 1.75 users online at any given moment:
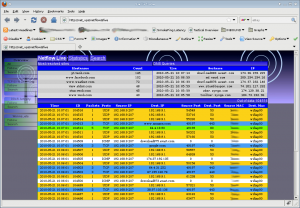
I’ve also started working on writing a Netflow analyzer application, based off a similar application I wrote for work. At the current time, this version only streams real-time connection endpoints and DNS statistics (last resolved sites, most resolved sites), as well as detects TCP SYN scans. Each flow record is also colorized (similar to what you would see in Wireshark), to further categorize the type of connection.
Instead of calling the gethostbyaddr() function on a destination IP (which simply pulls a PTR record, and in the world of vhosts is a poor representation of where a user is actually connecting), subscriber DNS queries are syslogged offsite and parsed. The Netflow Live application I’m building uses those parsed and stored queries to give a fairly accurate determination of what site is being visited when.
Visited URLs could also be determined and logged if a transparent Squid proxy was utilized on the Access Points. I have NO intention of doing this, however. I’m only concerned with endpoints and protocols being used. The number one protocol in use on the network: HTTP (Shocking!)
For those of you unfamiliar with Netflow, it’s a solution put forth by Cisco for IP traffic profiling. The two main elements are an exporter (usually a router) and a collector (which the exporter sends flow data to). Netflow does not include data payloads , ONLY a log of the endpoints used in each connection. (Think of it this way: When you make a long distance phone-call, you receive a monthly bill that details your phone number called another phone number at a specific time, for a specific duration. The phone company doesn’t actually have record of the conversation, however).
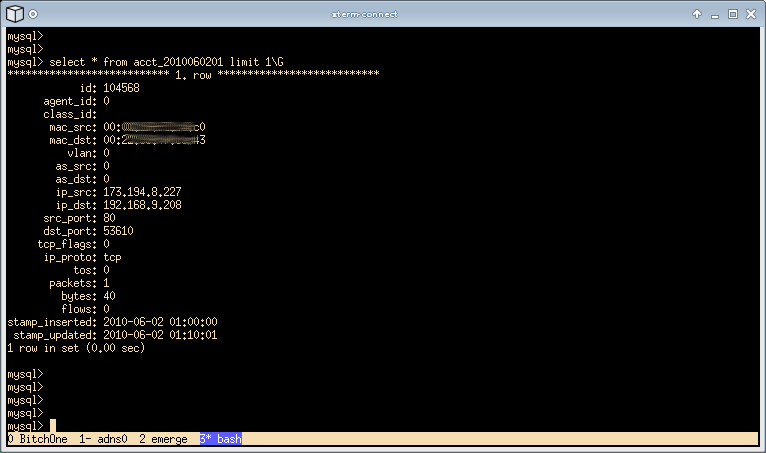
The data collected does include IP source and destination addresses, Transport layer source and destination ports, byte countes, packet counts, TCP flags, and MAC addresses. (Below is all the fields actually captured)
So what does this allow? Utilizing Netflow, I can determine subscribers on the network with certain network signatures for viruses, detect some DoS attacks and SYN scans, and graph the most commonly used protocols on the network.
I can also shape traffic based on determinations made by looking at the data. Is someone experiencing bad Skype calls due to someone streaming video over HTTP? I can use the netflow data to reshape things as needed.
So what’s in the works? Using NetGeo data, I plan on mapping connection endpoints on a US world map, allowing a visual display of where in the world most connections are destined.
But next up: I need to fix the bug preventing a software reboot of the access points – hopefully I can get to that this weekend.
Update 6/9/2010:
Jake Wilson pointed out the free NetFlow analyzer Scrutinizer by Plixer. I’ve not had a chance to look it over yet – but check out this video about the product. I first came across that video a month or two ago… it was like staring at the sun, initially I couldn’t tell if I liked it or not – but I watched it like 20 times that day. GREAT work guys, catchy AND entertaining.