I’m just finishing up a CCNA preparatory class at the local community college (I had no idea what to expect on the exam, so thankfully I stumbled across this class). I’d definitely recommend the course – the instructor (Shawn Cannady) has done an excellent job covering a wide volume of material in a rapid pace.
One of my classmates recently asked about how I was segmenting off the public wireless from my home LAN. As VLANs, VTPs and PPP were subjects covered in the course, I wrote the following article for the class Wiki:
In the United States, many (but not all) providers use PPPoE to establish the layer 2 connection over ADSL. The upside to this method is increased accountability/manageability, as well as the ability to resell the connection to 3rd parties (For non-resold lines, Telcos are shifting to DHCP-only connections however, as there’s less overhead involved)
Background: Many smaller ISPs use the local Telco DSLAM equipment along with dedicated circuitry and L2TP tunnels back to the smaller ISP routers – which terminate the PPP sessions. In such an instance, connections are routed to individual ISPs based on the realm in the authenticating username [username@realm.com/password]. The smaller ISP can then use their ARIN assigned network to assign globally routed IP addresses.
Working for such an ISP, I often take advantage of this setup – creating new PPPoE username and passwords on our system for individualized connections. Instead of having 3 separate ADSL lines for 3 different Internet connections, I use 1 single ADSL line for 3 different Internet connections. Each “unique” connection has it’s own PPPoE username/password and IP. (The only downside: Each connection shares the bandwidth of the 1 line).
The upside to this configuration is the isolation of Layer 3 – not all connections pass through the same router on my end of the connection. They do, however, pass through the same switch(es) and ADSL modem (however, at layer 2). Instead of worrying about access-lists to prevent different subnets from communicating with each other, I simply worry about inbound traffic from the WAN side on each connection.
My current home layout (simplified here) contains 2 switches. Switch A is located in my office, while Switch B is located where the phone line enters the upstairs. VLAN 2 connects devices directly to the ADSL modem. VLAN1 connects my home LAN to the LAN ethernet of my main home router.
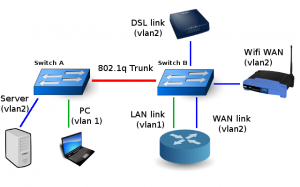
In the above layout, any device connecting to the DSL Link (members of VLAN2), must maintain it’s own PPPoE link to be able to access the Internet. (To simplify this image – imagine that the Wifi router is plugged directly into the DSL modem and configured to connect using PPPoE. Then, imagine the same thing for all members of VLAN 2)
An 802.1q trunk allows the server in my office direct connection to the ADSL modem, and allows my office LAN to connect to the main router (which in turn, routes traffic out the WAN interface PPPoE connection). There are numerous other devices on the LAN.
But why do this???
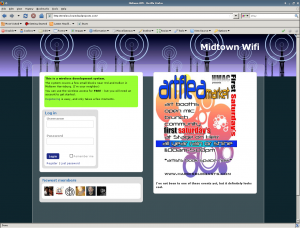
When I initially decided to provide free wireless access to my neighborhood, I had a few requirements. First of all, I did not want my neighbors connecting to my home LAN. Second, for liability reasons I wanted to the free WIFI to have it’s own globally routed IP address (not an RFC-1918 address NATed with my home static IP). A third requirement was the use of Netflow version 9 to collect various headers from each packet and frame (but not the data payload itself) in the event someone attempted something malicious or a user had major virus issues.
In addition to the WIFI access, on occassion I run dedicated honeypots and malware collectors – obviously servers you want completely isolated from your home LAN.
The above layout is by no means entirely bulletproof, but the added complexity means I don’t have to look over my shoulder as much — and I don’t have to maintain access-lists just for the LAN to live in “separated harmony”